IPV4设置
IPV4开启内网伪装
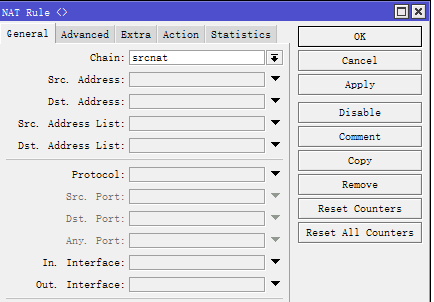
IP——Firewall——NET——添加规则
General中Chain:srcnat
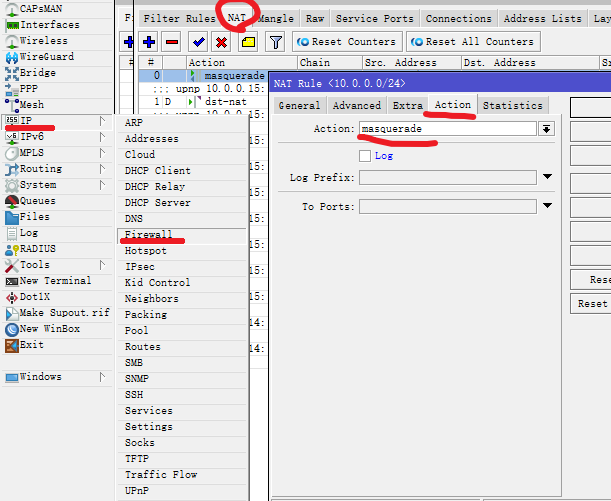
Action中Action:masquerad
排除所有来自外网的ping
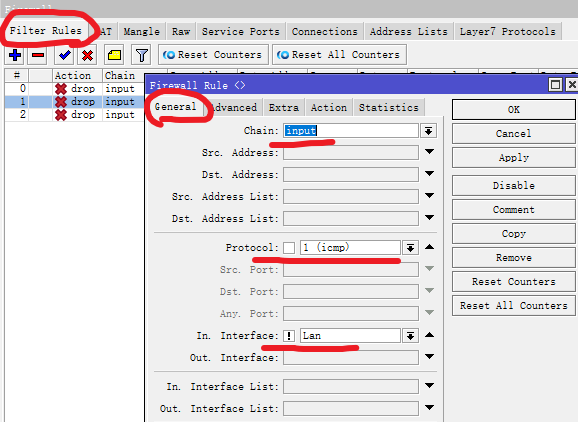
Filter Rules——General
chain:input
Protocol:1(ICMP)
In.interface:!Lan(!为排除)
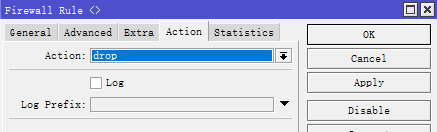
Action:drop
增强WinBox安全登录
IP——Services
关掉除Winbos外所有登录方式,修改端口号Port
Available From改为内网网段(例如:192.168.0.0/24)
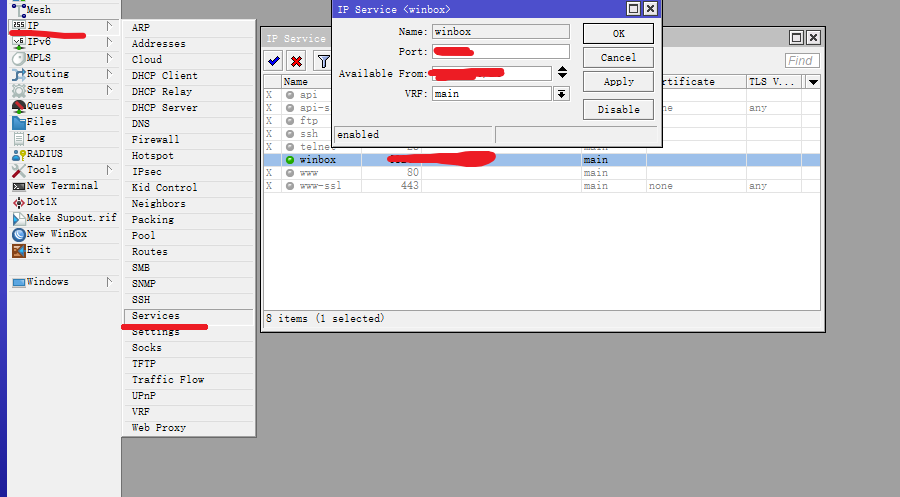
再次进入防火墙Filter Rules中新建一条规则
Filter Rules——General
chain:input
Protocol:6(tcp)
Dst.Port:设置为Winbox端口号
In.interface:!Lan(!为排除)
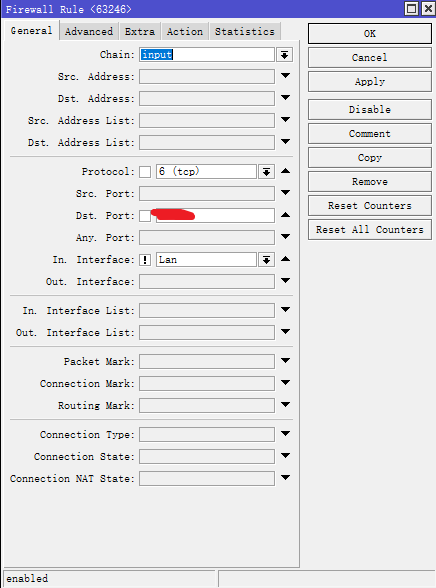
Action:drop
IPV6设置
官网参考文档:
https://help.mikrotik.com/docs/display/ROS/Building+Advanced+Firewall
转载于另一个参考连接,仅供个人备份
https://gitee.com/callmer/routeros_toss_notes/blob/master/09.%E8%AE%BE%E7%BD%AEIPv6.md
| 联网模式 | 内网 DNS | 防火墙模式 | 配置脚本 |
|---|---|---|---|
| PPPoE | 否 | 高级1 | ros_firewall_ipv6_pppoe.conf |
| 是 | 高级2 | ros_firewall_ipv6_pppoe_dns.conf | |
| 否 | 精简 | ros_firewall_ipv6_pppoe_simple.conf |
## Filter 规则 18 条
## NAT 规则 3 条
## Mangle 规则 1 条
## Raw 规则 48 条
## Address-list 规则 17 条
/ipv6 firewall address-list
add address=fe80::/10 comment="defconf: RFC6890 Linked-Scoped Unicast" list=no_forward_ipv6
add address=ff00::/8 comment="defconf: multicast" list=no_forward_ipv6
add address=::1/128 comment="defconf: RFC6890 lo" list=bad_ipv6
add address=::ffff:0:0/96 comment="defconf: RFC6890 IPv4 mapped" list=bad_ipv6
add address=2001::/23 comment="defconf: RFC6890" list=bad_ipv6
add address=2001:db8::/32 comment="defconf: RFC6890 documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: RFC6890 orchid" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: RFC6890 Discard-only" list=not_global_ipv6
add address=2001::/32 comment="defconf: RFC6890 TEREDO" list=not_global_ipv6
add address=2001:2::/48 comment="defconf: RFC6890 Benchmark" list=not_global_ipv6
add address=fc00::/7 comment="defconf: RFC6890 Unique-Local" list=not_global_ipv6
add address=::/128 comment="defconf: unspecified" list=bad_dst_ipv6
add address=::/128 comment="defconf: unspecified" list=bad_src_ipv6
add address=ff00::/8 comment="defconf: multicast" list=bad_src_ipv6
add address=::/128 comment="ddosconf: DDoS" list=ddos_targets_ipv6
add address=::/128 comment="ddosconf: DDoS" list=ddos_attackers_ipv6
/ipv6 firewall filter
add action=accept chain=input comment="defconf: accept ICMPv6 after RAW" protocol=icmpv6
add action=accept chain=input comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept UDP traceroute" port=33434-33534 protocol=udp
add action=accept chain=input comment="defconf: accept DHCPv6-Client prefix delegation" dst-port=546 protocol=udp src-address=fe80::/10 log=yes log-prefix="[ipv6-pd]"
add action=drop chain=input comment="defconf: drop all not coming from LAN" in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop bad forward IPs" src-address-list=no_forward_ipv6
add action=drop chain=forward comment="defconf: drop bad forward IPs" dst-address-list=no_forward_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6 after RAW" protocol=icmpv6
add action=drop chain=forward comment="defconf: drop everything else not coming from LAN" in-interface-list=!LAN
add action=jump chain=forward comment="ddosconf: DDoS" connection-state=new jump-target=detect-ddos
add action=return chain=detect-ddos comment="ddosconf: DDoS SYN-ACK Flood" dst-limit=50,50,src-and-dst-addresses/10s protocol=tcp tcp-flags=syn,ack log=yes log-prefix="[syn-ack-flood]"
add action=return chain=detect-ddos comment="ddosconf: DDoS" dst-limit=200,200,src-and-dst-addresses/10s
add action=add-dst-to-address-list chain=detect-ddos comment="ddosconf: DDoS" address-list=ddos_targets_ipv6 address-list-timeout=10m
add action=add-src-to-address-list chain=detect-ddos comment="ddosconf: DDoS" address-list=ddos_attackers_ipv6 address-list-timeout=10m log=yes log-prefix="[ddos-ipv6]"
/ipv6 firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade IPv6" out-interface-list=WAN disabled=yes
add action=redirect chain=dstnat comment="lanconf: redirect DNS query (UDP)" dst-port=53 in-interface-list=LAN protocol=udp to-ports=53
add action=redirect chain=dstnat comment="lanconf: redirect DNS query (TCP)" dst-port=53 in-interface-list=LAN protocol=tcp to-ports=53
/ipv6 firewall mangle
add action=change-mss chain=forward comment="defconf: fix IPv6 mss for WAN" new-mss=clamp-to-pmtu passthrough=yes protocol=tcp tcp-flags=syn
/ipv6 firewall raw
add action=accept chain=prerouting comment="defconf: enable for transparent firewall" disabled=yes
add action=drop chain=prerouting comment="ddosconf: DDoS" dst-address-list=ddos_targets_ipv6 src-address-list=ddos_attackers_ipv6
add action=drop chain=prerouting comment="defconf: drop IPv6 extension headers types 0,43" headers=hop,route:contains
add action=accept chain=prerouting comment="defconf: RFC4291, section 2.7.1" dst-address=ff02:0:0:0:0:1:ff00::/104 icmp-options=135 protocol=icmpv6 src-address=::/128
add action=drop chain=prerouting comment="defconf: drop bogon IPs" src-address-list=bad_ipv6
add action=drop chain=prerouting comment="defconf: drop bogon IPs" dst-address-list=bad_ipv6
add action=drop chain=prerouting comment="defconf: drop packets with bad SRC ipv6" src-address-list=bad_src_ipv6
add action=drop chain=prerouting comment="defconf: drop packets with bad DST ipv6" dst-address-list=bad_dst_ipv6
add action=drop chain=prerouting comment="defconf: drop non global from WAN" in-interface-list=WAN src-address-list=not_global_ipv6
add action=drop chain=prerouting comment="defconf: drop UDP port 0" port=0 protocol=udp log=yes log-prefix="[udp-port-0]"
add action=jump chain=prerouting comment="defconf: jump to ICMPv6 chain" jump-target=icmp6 protocol=icmpv6
add action=jump chain=prerouting comment="defconf: jump to TCP chain" jump-target=bad-tcp protocol=tcp
add action=accept chain=prerouting comment="defconf: accept local multicast scope" dst-address=ff02::/16
add action=drop chain=prerouting comment="defconf: drop other multicast destinations" dst-address=ff00::/8
add action=accept chain=prerouting comment="defconf: accept everything else from LAN" in-interface-list=LAN
add action=accept chain=prerouting comment="defconf: accept everything else from WAN" in-interface-list=WAN
add action=drop chain=prerouting comment="defconf: drop the rest"
add action=drop chain=bad-tcp comment="defconf: TCP flag filter" protocol=tcp tcp-flags=!fin,!syn,!rst,!ack
add action=drop chain=bad-tcp comment="defconf: drop flags fin,syn" protocol=tcp tcp-flags=fin,syn
add action=drop chain=bad-tcp comment="defconf: drop flags fin,rst" protocol=tcp tcp-flags=fin,rst
add action=drop chain=bad-tcp comment="defconf: drop flags fin,!ack" protocol=tcp tcp-flags=fin,!ack
add action=drop chain=bad-tcp comment="defconf: drop flags fin,urg" protocol=tcp tcp-flags=fin,urg
add action=drop chain=bad-tcp comment="defconf: drop flags syn,rst" protocol=tcp tcp-flags=syn,rst
add action=drop chain=bad-tcp comment="defconf: drop flags rst,urg" protocol=tcp tcp-flags=rst,urg
add action=drop chain=bad-tcp comment="defconf: drop TCP port 0" port=0 protocol=tcp log=yes log-prefix="[tcp-port-0]"
add action=accept chain=icmp6 comment="defconf: rfc4890 drop ll if hop-limit!=255" dst-address=fe80::/10 hop-limit=not-equal:255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 DST unreachable" icmp-options=1:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 packet too big" icmp-options=2:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 time exceeded" icmp-options=3:0-1 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 parameter problem" icmp-options=4:0-2 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 echo request" icmp-options=128:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 echo response" icmp-options=129:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener query only LAN" src-address=fe80::/10 icmp-options=130:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener query report only LAN" src-address=fe80::/10 icmp-options=131:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener query done only LAN" src-address=fe80::/10 icmp-options=132:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 router solic only LAN" hop-limit=equal:255 icmp-options=133:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 router advert only LAN" hop-limit=equal:255 icmp-options=134:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 neighbor solic only LAN" hop-limit=equal:255 icmp-options=135:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 neighbor advert only LAN" hop-limit=equal:255 icmp-options=136:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 inverse ND solic only LAN" hop-limit=equal:255 icmp-options=141:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 inverse ND advert only LAN" hop-limit=equal:255 icmp-options=142:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener report v2 only LAN" src-address=fe80::/10 icmp-options=143:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 certificate path solicitation only LAN" hop-limit=equal:255 icmp-options=148:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 certificate path advertisement only LAN" hop-limit=equal:255 icmp-options=149:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast router advertisement only LAN" src-address=fe80::/10 hop-limit=equal:1 icmp-options=151:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast router solicitation only LAN" src-address=fe80::/10 hop-limit=equal:1 icmp-options=152:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast router termination only LAN" src-address=fe80::/10 hop-limit=equal:1 icmp-options=153:0-255 in-interface-list=LAN protocol=icmpv6
add action=drop chain=icmp6 comment="defconf: drop all other ICMPv6" protocol=icmpv6高级2
## Filter 规则 18 条
## NAT 规则 5 条
## Mangle 规则 1 条
## Raw 规则 48 条
## Address-list 规则 19 条
/ipv6 firewall address-list
add address=fdac::2 comment="lanconf: local DNS server" list=local_dns_ipv6
add address=fdac::3 comment="lanconf: local DNS server" list=local_dns_ipv6
add address=fe80::/10 comment="defconf: RFC6890 Linked-Scoped Unicast" list=no_forward_ipv6
add address=ff00::/8 comment="defconf: multicast" list=no_forward_ipv6
add address=::1/128 comment="defconf: RFC6890 lo" list=bad_ipv6
add address=::ffff:0:0/96 comment="defconf: RFC6890 IPv4 mapped" list=bad_ipv6
add address=2001::/23 comment="defconf: RFC6890" list=bad_ipv6
add address=2001:db8::/32 comment="defconf: RFC6890 documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: RFC6890 orchid" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: RFC6890 Discard-only" list=not_global_ipv6
add address=2001::/32 comment="defconf: RFC6890 TEREDO" list=not_global_ipv6
add address=2001:2::/48 comment="defconf: RFC6890 Benchmark" list=not_global_ipv6
add address=fc00::/7 comment="defconf: RFC6890 Unique-Local" list=not_global_ipv6
add address=::/128 comment="defconf: unspecified" list=bad_dst_ipv6
add address=::/128 comment="defconf: unspecified" list=bad_src_ipv6
add address=ff00::/8 comment="defconf: multicast" list=bad_src_ipv6
add address=::/128 comment="ddosconf: DDoS" list=ddos_targets_ipv6
add address=::/128 comment="ddosconf: DDoS" list=ddos_attackers_ipv6
/ipv6 firewall filter
add action=accept chain=input comment="defconf: accept ICMPv6 after RAW" protocol=icmpv6
add action=accept chain=input comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept UDP traceroute" port=33434-33534 protocol=udp
add action=accept chain=input comment="defconf: accept DHCPv6-Client prefix delegation" dst-port=546 protocol=udp src-address=fe80::/10 log=yes log-prefix="[ipv6-pd]"
add action=drop chain=input comment="defconf: drop all not coming from LAN" in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop bad forward IPs" src-address-list=no_forward_ipv6
add action=drop chain=forward comment="defconf: drop bad forward IPs" dst-address-list=no_forward_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6 after RAW" protocol=icmpv6
add action=drop chain=forward comment="defconf: drop everything else not coming from LAN" in-interface-list=!LAN
add action=jump chain=forward comment="ddosconf: DDoS" connection-state=new jump-target=detect-ddos
add action=return chain=detect-ddos comment="ddosconf: DDoS SYN-ACK Flood" dst-limit=50,50,src-and-dst-addresses/10s protocol=tcp tcp-flags=syn,ack log=yes log-prefix="[syn-ack-flood]"
add action=return chain=detect-ddos comment="ddosconf: DDoS" dst-limit=200,200,src-and-dst-addresses/10s
add action=add-dst-to-address-list chain=detect-ddos comment="ddosconf: DDoS" address-list=ddos_targets_ipv6 address-list-timeout=10m
add action=add-src-to-address-list chain=detect-ddos comment="ddosconf: DDoS" address-list=ddos_attackers_ipv6 address-list-timeout=10m log=yes log-prefix="[ddos-ipv6]"
/ipv6 firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade IPv6" out-interface-list=WAN disabled=yes
add action=accept chain=dstnat comment="lanconf: accept local DNS server's query (UDP)" dst-port=53 in-interface-list=LAN protocol=udp src-address-list=local_dns_ipv6
add action=accept chain=dstnat comment="lanconf: accept local DNS server's query (TCP)" dst-port=53 in-interface-list=LAN protocol=tcp src-address-list=local_dns_ipv6
add action=redirect chain=dstnat comment="lanconf: redirect DNS query (UDP)" dst-port=53 in-interface-list=LAN protocol=udp to-ports=53
add action=redirect chain=dstnat comment="lanconf: redirect DNS query (TCP)" dst-port=53 in-interface-list=LAN protocol=tcp to-ports=53
/ipv6 firewall mangle
add action=change-mss chain=forward comment="defconf: fix IPv6 mss for WAN" new-mss=clamp-to-pmtu passthrough=yes protocol=tcp tcp-flags=syn
/ipv6 firewall raw
add action=accept chain=prerouting comment="defconf: enable for transparent firewall" disabled=yes
add action=drop chain=prerouting comment="ddosconf: DDoS" dst-address-list=ddos_targets_ipv6 src-address-list=ddos_attackers_ipv6
add action=drop chain=prerouting comment="defconf: drop IPv6 extension headers types 0,43" headers=hop,route:contains
add action=accept chain=prerouting comment="defconf: RFC4291, section 2.7.1" dst-address=ff02:0:0:0:0:1:ff00::/104 icmp-options=135 protocol=icmpv6 src-address=::/128
add action=drop chain=prerouting comment="defconf: drop bogon IPs" src-address-list=bad_ipv6
add action=drop chain=prerouting comment="defconf: drop bogon IPs" dst-address-list=bad_ipv6
add action=drop chain=prerouting comment="defconf: drop packets with bad SRC ipv6" src-address-list=bad_src_ipv6
add action=drop chain=prerouting comment="defconf: drop packets with bad DST ipv6" dst-address-list=bad_dst_ipv6
add action=drop chain=prerouting comment="defconf: drop non global from WAN" in-interface-list=WAN src-address-list=not_global_ipv6
add action=drop chain=prerouting comment="defconf: drop UDP port 0" port=0 protocol=udp log=yes log-prefix="[udp-port-0]"
add action=jump chain=prerouting comment="defconf: jump to ICMPv6 chain" jump-target=icmp6 protocol=icmpv6
add action=jump chain=prerouting comment="defconf: jump to TCP chain" jump-target=bad-tcp protocol=tcp
add action=accept chain=prerouting comment="defconf: accept local multicast scope" dst-address=ff02::/16
add action=drop chain=prerouting comment="defconf: drop other multicast destinations" dst-address=ff00::/8
add action=accept chain=prerouting comment="defconf: accept everything else from LAN" in-interface-list=LAN
add action=accept chain=prerouting comment="defconf: accept everything else from WAN" in-interface-list=WAN
add action=drop chain=prerouting comment="defconf: drop the rest"
add action=drop chain=bad-tcp comment="defconf: TCP flag filter" protocol=tcp tcp-flags=!fin,!syn,!rst,!ack
add action=drop chain=bad-tcp comment="defconf: drop flags fin,syn" protocol=tcp tcp-flags=fin,syn
add action=drop chain=bad-tcp comment="defconf: drop flags fin,rst" protocol=tcp tcp-flags=fin,rst
add action=drop chain=bad-tcp comment="defconf: drop flags fin,!ack" protocol=tcp tcp-flags=fin,!ack
add action=drop chain=bad-tcp comment="defconf: drop flags fin,urg" protocol=tcp tcp-flags=fin,urg
add action=drop chain=bad-tcp comment="defconf: drop flags syn,rst" protocol=tcp tcp-flags=syn,rst
add action=drop chain=bad-tcp comment="defconf: drop flags rst,urg" protocol=tcp tcp-flags=rst,urg
add action=drop chain=bad-tcp comment="defconf: drop TCP port 0" port=0 protocol=tcp log=yes log-prefix="[tcp-port-0]"
add action=accept chain=icmp6 comment="defconf: rfc4890 drop ll if hop-limit!=255" dst-address=fe80::/10 hop-limit=not-equal:255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 DST unreachable" icmp-options=1:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 packet too big" icmp-options=2:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 time exceeded" icmp-options=3:0-1 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 parameter problem" icmp-options=4:0-2 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 echo request" icmp-options=128:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 echo response" icmp-options=129:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener query only LAN" src-address=fe80::/10 icmp-options=130:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener query report only LAN" src-address=fe80::/10 icmp-options=131:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener query done only LAN" src-address=fe80::/10 icmp-options=132:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 router solic only LAN" hop-limit=equal:255 icmp-options=133:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 router advert only LAN" hop-limit=equal:255 icmp-options=134:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 neighbor solic only LAN" hop-limit=equal:255 icmp-options=135:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 neighbor advert only LAN" hop-limit=equal:255 icmp-options=136:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 inverse ND solic only LAN" hop-limit=equal:255 icmp-options=141:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 inverse ND advert only LAN" hop-limit=equal:255 icmp-options=142:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener report v2 only LAN" src-address=fe80::/10 icmp-options=143:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 certificate path solicitation only LAN" hop-limit=equal:255 icmp-options=148:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 certificate path advertisement only LAN" hop-limit=equal:255 icmp-options=149:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast router advertisement only LAN" src-address=fe80::/10 hop-limit=equal:1 icmp-options=151:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast router solicitation only LAN" src-address=fe80::/10 hop-limit=equal:1 icmp-options=152:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast router termination only LAN" src-address=fe80::/10 hop-limit=equal:1 icmp-options=153:0-255 in-interface-list=LAN protocol=icmpv6
add action=drop chain=icmp6 comment="defconf: drop all other ICMPv6" protocol=icmpv6
精简
## Filter 规则 13 条
## NAT 规则 3 条
## Mangle 规则 1 条
## Address-list 规则 9 条
/ipv6 firewall address-list
add list=bad_ipv6 address=::/128 comment="defconf: unspecified address"
add list=bad_ipv6 address=::1 comment="defconf: lo"
add list=bad_ipv6 address=fec0::/10 comment="defconf: site-local"
add list=bad_ipv6 address=::ffff:0:0/96 comment="defconf: ipv4-mapped"
add list=bad_ipv6 address=::/96 comment="defconf: ipv4 compat"
add list=bad_ipv6 address=100::/64 comment="defconf: discard only "
add list=bad_ipv6 address=2001:db8::/32 comment="defconf: documentation"
add list=bad_ipv6 address=2001:10::/28 comment="defconf: ORCHID"
add list=bad_ipv6 address=3ffe::/16 comment="defconf: 6bone"
/ipv6 firewall filter
add chain=input action=accept connection-state=established,related,untracked comment="defconf: accept established,related,untracked"
add chain=input action=drop connection-state=invalid comment="defconf: drop invalid"
add chain=input action=accept protocol=icmpv6 comment="defconf: accept ICMPv6"
add chain=input action=accept protocol=udp port=33434-33534 comment="defconf: accept UDP traceroute"
add chain=input action=accept protocol=udp dst-port=546 src-address=fe80::/10 comment="defconf: accept DHCPv6-Client prefix delegation" log=yes log-prefix="[ipv6-pd]"
add chain=input action=drop in-interface-list=!LAN comment="defconf: drop everything else not coming from LAN"
add chain=forward action=accept connection-state=established,related,untracked comment="defconf: accept established,related,untracked"
add chain=forward action=drop connection-state=invalid comment="defconf: drop invalid"
add chain=forward action=drop src-address-list=bad_ipv6 comment="defconf: drop packets with bad src ipv6"
add chain=forward action=drop dst-address-list=bad_ipv6 comment="defconf: drop packets with bad dst ipv6"
add chain=forward action=drop protocol=icmpv6 hop-limit=equal:1 comment="defconf: rfc4890 drop hop-limit=1"
add chain=forward action=accept protocol=icmpv6 comment="defconf: accept ICMPv6"
add chain=forward action=drop in-interface-list=!LAN comment="defconf: drop everything else not coming from LAN"
/ipv6 firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade IPv6" out-interface-list=WAN disabled=yes
add action=redirect chain=dstnat comment="lanconf: redirect DNS query (UDP)" dst-port=53 in-interface-list=LAN protocol=udp to-ports=53
add action=redirect chain=dstnat comment="lanconf: redirect DNS query (TCP)" dst-port=53 in-interface-list=LAN protocol=tcp to-ports=53
/ipv6 firewall mangle
add action=change-mss chain=forward comment="defconf: fix IPv6 mss for WAN" new-mss=clamp-to-pmtu passthrough=yes protocol=tcp tcp-flags=syn设置 IPv6 黑洞路由
## 根据 RFC6890 创建 IPv6 黑洞路由
## 规则 13 条
/ipv6 route
add blackhole comment="defconf: RFC6890 - loopback address" disabled=no dst-address=::1/128
add blackhole comment="defconf: RFC6890 - unspecified address" disabled=no dst-address=::/128
add blackhole comment="defconf: RFC6890 - IPv4-IPv6 translate" disabled=no dst-address=64:ff9b::/96
add blackhole comment="defconf: RFC6890 - IPv4-mapped address" disabled=no dst-address=::ffff:0:0/96
add blackhole comment="defconf: RFC6890 - discard-only address block" disabled=no dst-address=100::/64
add blackhole comment="defconf: RFC6890 - IETF protocol assignments" disabled=no dst-address=2001::/23
add blackhole comment="defconf: RFC6890 - TEREDO" disabled=no dst-address=2001::/32
add blackhole comment="defconf: RFC6890 - benchmarking" disabled=no dst-address=2001:2::/48
add blackhole comment="defconf: RFC6890 - documentation" disabled=no dst-address=2001:db8::/32
add blackhole comment="defconf: RFC6890 - ORCHID" disabled=no dst-address=2001:10::/28
add blackhole comment="defconf: RFC6890 - 6to4" disabled=no dst-address=2002::/16
add blackhole comment="defconf: RFC6890 - unique-local" disabled=no dst-address=fc00::/7
add blackhole comment="defconf: RFC6890 - linked-scoped unicast" disabled=no dst-address=fe80::/10